The search engine that doesn’t track you.
The Tor software protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, it prevents the sites you visit from learning your physical location, and it lets you access sites which are blocked.
Would you fall for a phishing attack trick? Try this online quiz.
Test your home router (Note: This is part a home digital security commercial solicitation)
“Protecting Your Digital Life in 8 Easy Steps” – NYT
Signal messages and calls are always end-to-end encrypted and painstakingly engineered to keep your communication safe. We can’t read your messages or see your calls, and no one else can either.
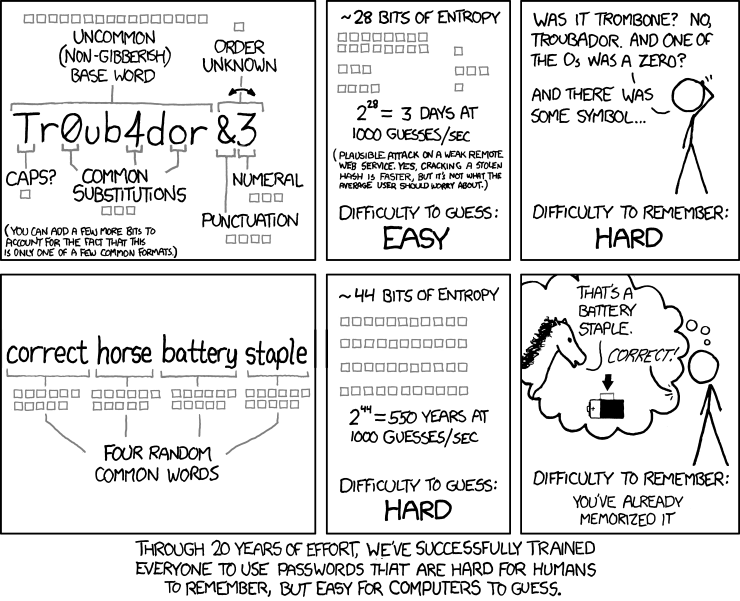
One of the most effective methods of cyber attack is to simply use your password. Hackers can get a hold of your password through strategies such as brute force and social engineering. This is why is essential that you have strong passwords and that you do not share them. Here are some resources to help you create strong passwords and keep them safe.
From XKCD:
“This List Of 2014’s Worst Passwords, Including ‘123456,’ Is Embarrassing” | TechCrunch
“The best password managers for PCs, Macs, and mobile devices” – ITworld
The Apple iOS 11 Privacy and Security Settings You Should Check | WIRED